EXCLUSIVE= National Archives to release hundreds of letters between the Queen and Governors-General.
The National Archives of Australia is set to release decades of correspondence between the Queen and Governors-General, from Sir Richard Casey in 1965 to Bill Hayden in 1996. The decision follows the High Court’s ruling in my landmark ‘Palace letters’ case against the Archives which, in May 2020, overturned the Queen’s embargo over her correspondence with Governor-General Sir John Kerr, much of it relating to the dismissal of the Whitlam government. Continue reading
Politico – The government doesn’t do much to verify the security of software from private contractors. And that’s how suspected Russian hackers got in: “The massive monthslong hack of agencies across the U.S. government succeeded, in part, because no one was looking in the right place. The federal government conducts only cursory security inspections of the software it buys from private companies for a wide range of activities, from managing databases to operating internal chat applications. That created the blind spot that suspected Russian hackers exploited to breach the Treasury Department, the Department of Homeland Security, the National Institutes of Health and other agencies. After embedding code in widely used network management software made by a Texas company called SolarWinds, all they had to do was wait for the agencies to download routine software updates from the trusted supplier…
The SolarWinds hack — which officials have linked to Russia’s foreign intelligence service, the SVR and which Secretary of State Mike Pompeo late Friday publicly pinned on Russia — reflects a level of sophistication that may be impossible to completely block, but technical professionals and policymakers say new approaches to software development and procurement could at least give defenders a fighting chance…”
MIT Technology Review – And why it could take months more to discover how many other governments and companies have been breached – “To carry out the breach, the hackers first broke into the systems of SolarWinds, an American software company. There, they inserted a back door into Orion, one of the company’s products, which organizations use to see and manage vast internal networks of computers. For several weeks beginning in March, any client that updated to the latest version of Orion—digitally signed by SolarWinds, and therefore seemingly legitimate—unwittingly downloaded the compromised software, giving the hackers a way into their systems. SolarWinds has around 300,000 customers around the world, including most of the Fortune 500 and many governments. In a new filing with the Securities and Exchange Commission, the firm said “fewer than” 18,000 organizations ever downloaded the compromised update. (SolarWinds said it’s not clear yet how many of those systems were actually hacked.) Standard cybersecurity practice is to keep your software up to date—so most SolarWinds customers, ironically, were protected because they had failed to heed that advice. The hackers were “extremely clever and strategic,” says Greg Touhill, a former federal chief information security officer. Even once they had gained access through the back door in Orion, known as Sunburst, they moved slowly and deliberately. Instead of infiltrating many systems at once, which could easily have raised suspicions, they focused on a small set of selected targets, according to a report from the security firm FireEye…”
Conspiracy Theories, by Jared Millson (California State-Bakersfield).
What Is It To Love Someone?, by Felipe Pereira (Pittsburgh).
Think Least of Death: Spinoza on How to Live and How to Die, by Steven Nadler, reviewed by Carlos Fraenkel at Boston Review.
The Knowledge Machine, by Michael Strevens, reviewed by Christoph Irmscher at The Wall Street Journal
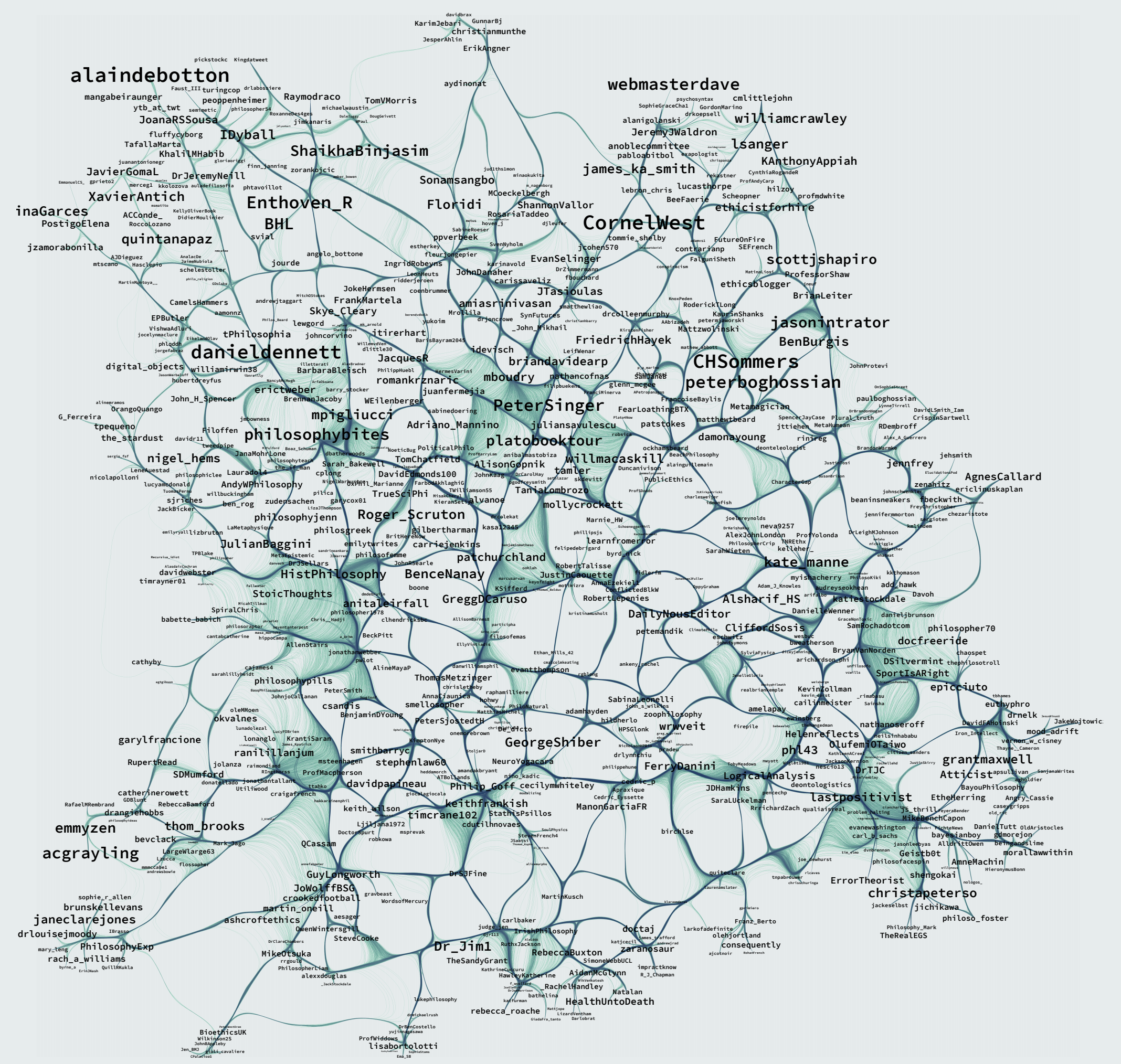
As a “fun Friday afternoon project,” Maximillian Noichl created a visualization of “the network of academic-philosophy-Twitter.”
It looks like this:
Noichl (@MaxNoichl), whose work has been featured here before, prompted by a query on Twitter from Helen De Cruz (@Helenreflects), based his visualization on the philosophy Twitter lists of Kelly Truelove (@truesciphi).
The image includes 791 philosopher accounts, each with at least 1,000 followers. “The philosophers are arranged by the similarity between the lists of accounts which they mention or retweet on their timeline, based on a sample of altogether 2,004,543 tweets,” Noichl says.
What does this visualization tell us? Noichl writes:
Accounts that are placed close together can be expected to share similar material, and I think we arrive at some meaningful clustering. Accounts that retweet each other are linked via edges, and the larger bundles of edges hint at the intensity of interaction between the corresponding clusters.
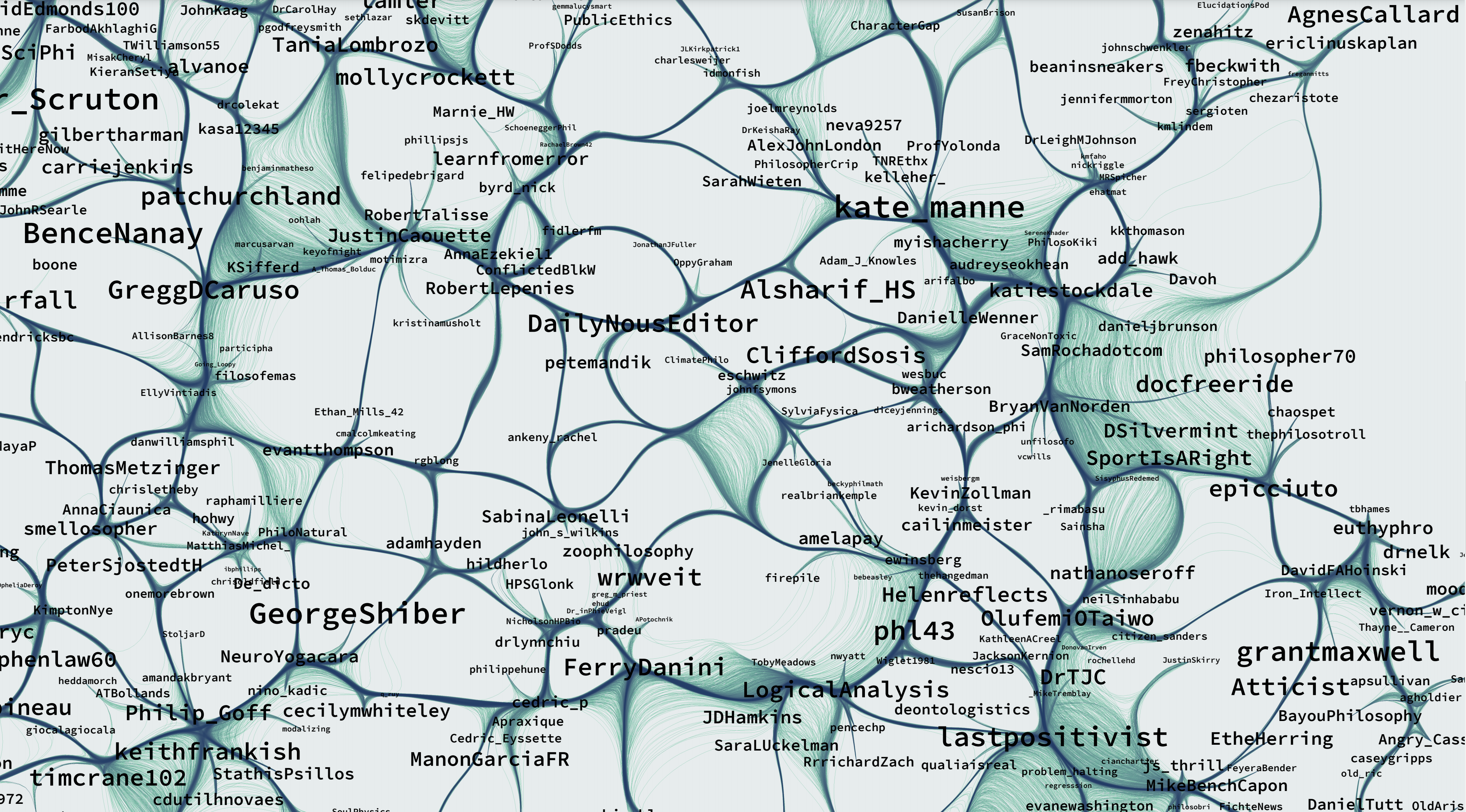
Here’s a slightly zoomed-in shot of part of it (you can click on the image to enlarge it):
At Noichl’s site, the image is a PDF that you can zoom in on and text-search to find specific accounts.