Julian Assange to seek release from prison after extradition ruling
It says plenty about the Chinese Communist Party’s lack of transparency that we still don’t know the origin of COVID-19.
As we head into an uncertain year with panicked politicians, hysterical media and a populace that’s been scared senseless, let us not forget how we got here and the role China has played in the death, destruction and hardship endured in 2020.
China is a rogue state and a danger to the world: Rita Panahi
DOD gives $2.5B to consortium to develop 5G tech prototypes
‘Passionate’ Belief in Freedom of Speech and Multiplying Orthodoxies
There is no midnight knock on the door, at least not yet, to ensure conformity, but those who question these little orthodoxies (whose content, incidentally, changes all the time, but also extends in scope, like multiplying starfish crawling over a coral reef) are subject to such punishments as ostracism or black-listing.
Louis Menand, The Free World: Art and Thought in the Cold War, a lengthy book due out in April 2021
Simmering Over a ‘Cyber Cold War’
New reports released this week on recent, high-profile data breaches make the compelling case that a simmering Cold War-style cyber arms race has emerged between the United States and China.
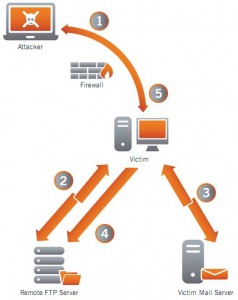 A study issued Thursday by McAfee and the Center for Strategic and International Studies found that more than half of the 600 executives surveyed worldwide said they had been subject to “stealthy infiltration” by high-level adversaries, and that 59 percent believed representatives of foreign governments had been involved in the attacks.
A study issued Thursday by McAfee and the Center for Strategic and International Studies found that more than half of the 600 executives surveyed worldwide said they had been subject to “stealthy infiltration” by high-level adversaries, and that 59 percent believed representatives of foreign governments had been involved in the attacks.
A more granular analysis issued Thursday by Mandiant, an Alexandria, Va. based security firm, focuses on data breaches it has responded to involving the so-called “advanced persistent threat,” or those characterized by highly targeted attacks using custom-made malicious software in the hands of patient, well-funded assailants.
Mandiant notes that the scale, operation and logistics of conducting these attacks – against the government, commercial and private sectors – indicates that they’re state-sponsored.
The Chinese government may authorize this activity, but there’s no way to determine the extent of its involvement. Nonetheless, we’ve been able to correlate almost every APT intrusion we’ve investigated to current events within China. In all cases, information exfiltrated by each set of attackers correlates with a need for intelligence related to upcoming major U.S. / China mergers and acquisitions, corporate business negotiations, or defense industrial base acquisition opportunities[emphasis added].
The reports come just days after the Christian Science Monitor revealed that three Texas-based oil companies – Conoco, ExxonMobil and Marathon – were alerted by the FBI that their systems were penetrated back in 2008. The Monitor story said the attacks, thought to have originated in China, targeted “bid data” about oil reserves and potential drilling sites.
Until this week, SolarWinds was a little known IT software group from Texas. Its deserted lobby has a framed magazine article from a few years ago when it was on a list of America’s “Best Small Companies”. Now the Austin-based company is at the heart of one of the biggest and most startling cyber hacks in recent history, with ramifications that extend into the fields of geopolitics, espionage and national security. For nine months, sophisticated state-backed hackers have exploited a ubiquitous SolarWinds software product in order to spy on government and business networks around the world, including in the US, UK, Israel and Canada. Wielding innovative tools and tradecraft, the cyber spies lurked in email services, and posed as legitimate staffers to tap confidential information stored in the cloud.
Beware of the burglars - Philadelphia Weekly.
Detectives and security specialists I’ve spoken to over the years say that most burglaries can be prevented. To avoid being burglarized, simply install an alarm system with cameras, place a sign in plain sight that states the property has an alarm system, and install good locks on the doors and windows. The cops see that many of the victims of burglary often have apparent security weaknesses that the burglars probably saw as well. The victims’ homes had no exterior lights, no alarm system, no signs and poor locks on the doors and windows.
Alphabet unit Wing blasts new U.S. drone ID rule, citing privacy Reuters
Google’s Wing warns new drone laws ‘may have unintended consequences’ for privacy The Verge Another reason not to use Amazon.
Hacked home cams used to livestream police raids in swatting attacks BBC
John le Carré on George Smiley: “Insofar as I am capable of self-love, I love him.”
Does David Cornwell — better known as John le Carré — admire George Smiley, his most celebrated spy? “He is the best of me, the most rational — I admire his commitment to his task and his sense of responsibility to humankind. Insofar as I am capable of self-love, I love him.”
